Network Efficiency Through MCP: EyeoTmonitor’s Real-World Results
- Understanding MCP in Network Monitoring Context
- EyeOTmonitor's MCP Integration Workflow
- Real-World Use Case: EOL Device Detection and Reporting
- Benefits Achieved Through MCP Implementation
- EyeOTmonitor’s Multi-Agent AI Ecosystem Focus
- Challenges and Lessons from the MCP Deployment
- Conclusion
- Key Takeaways
- FAQs
- References
Implementation of MCP not only streamlines security management but also enhances overall network performance by optimizing resource allocation. By leveraging real-time data analytics, organizations can proactively identify vulnerabilities and respond to threats more swiftly. This shift towards a more dynamic and responsive network environment is crucial in mitigating risks and ensuring compliance with evolving regulatory standards.
EyeOTmonitor has developed an MCP server implementation that demonstrates practical protocol applications in network environments. Our case study utilized n8n with an HTTPS Request node connecting to EyeOTmonitor APIs, combined with an MCP Server Trigger node. This MCP protocol implementation enabled direct integration with Claude Desktop, providing access to device information including IP addresses, firmware versions, severity levels, and hardware specifications.
The implementation's key capability involves automatic identification of end-of-life (EOL) devices across network infrastructure. When queried for EOL equipment, the system conducts independent research on vendor and model information, generating reports with specific EOL dates and mitigation recommendations. This automation reduces manual research time for IT teams while delivering actionable data for management decisions.
We will examine how this implementation enhanced network visibility, reduced manual research requirements, and streamlined reporting processes for more efficient network management.
Understanding MCP in Network Monitoring Context
Model Context Protocol (MCP) functions as a standardized framework enabling AI systems to connect with external data sources. Understanding its application in network monitoring requires examining the fundamental architecture and implementation approaches.
What is MCP Protocol and How It Works
Model Context Protocol operates through a client-server architecture with three primary components:
- MCP Host – The AI model (such as GPT-4, Claude, or Gemini) requesting data or actions
- MCP Client – An intermediary service forwarding AI model requests to MCP servers (examples include GitHub Copilot, Claude Desktop)
- MCP Server – Lightweight applications exposing specific capabilities through APIs, databases, or files
The protocol creates a universal connector for AI systems to interact with enterprise tools and data. This standardization addresses complexities associated with custom integrations, allowing developers to build more adaptable AI applications. MCP introduces clear security boundaries since hosts and servers communicate exclusively through the protocol, allowing security policies to be enforced at the protocol layer.
For network monitoring purposes, MCP servers translate requests into queries against data sources. This architecture enables modular, scalable solutions that respond to real-time signals across network infrastructure.
Why MCP is Relevant for Real-Time Network Insights
Real-time network monitoring requires immediate access to current data across diverse systems. MCP provides several advantages in this environment:
- Context Awareness – MCP allows AI models to access real-time data from multiple sources, improving their ability to provide relevant and current responses
- Standardized Integration – Rather than building custom connectors for each data source, MCP provides a universal method for connecting to various network monitoring tools
- Dynamic Discovery – AI models can query for available tools at runtime and decide how to use them based on current network conditions
- Security Controls – Built-in authentication and access control mechanisms ensure AI models only access authorized data
We have found MCP particularly valuable for querying device information across networks. Our implementation exposes details including IP addresses, firmware versions, vendor information, and severity levels. The protocol's standardization allows us to maintain secure boundaries during these operations, as discussed in our analysis of MCP security and compliance considerations.
MCP Server Implementation in n8n Workflows
Creating an effective MCP server implementation requires selecting the right platform and workflow automation tools. We chose n8n due to its flexibility and robust integration capabilities. The n8n platform facilitates MCP server creation through several key components.
The n8n MCP Trigger node functions as the entry point, enabling AI models to discover and interact with workflows. This node establishes the connection point for Claude Desktop or other MCP clients to access network monitoring data through our APIs.
We configured the HTTPS Request node to connect with EyeOTmonitor's APIs, allowing the MCP server to retrieve device information. This approach aligns with our broader comparison of MCP with other networking protocols like SNMP and NETCONF.
According to n8n documentation, workflows tagged for MCP availability can be discovered and executed by AI models through the Subworkflow trigger. This approach enables AI assistants to manage and run workflows independently, particularly valuable for complex network monitoring tasks.
n8n's MCP server implementation supports securing these connections with authentication methods, ensuring proper access controls. This architecture provides significant advantages over traditional network monitoring approaches, especially for identifying critical issues like EOL devices.
Our MCP implementation delivers capabilities for network analysis beyond basic monitoring. The system translates human queries about network status into actionable insights without requiring specialized query language knowledge.
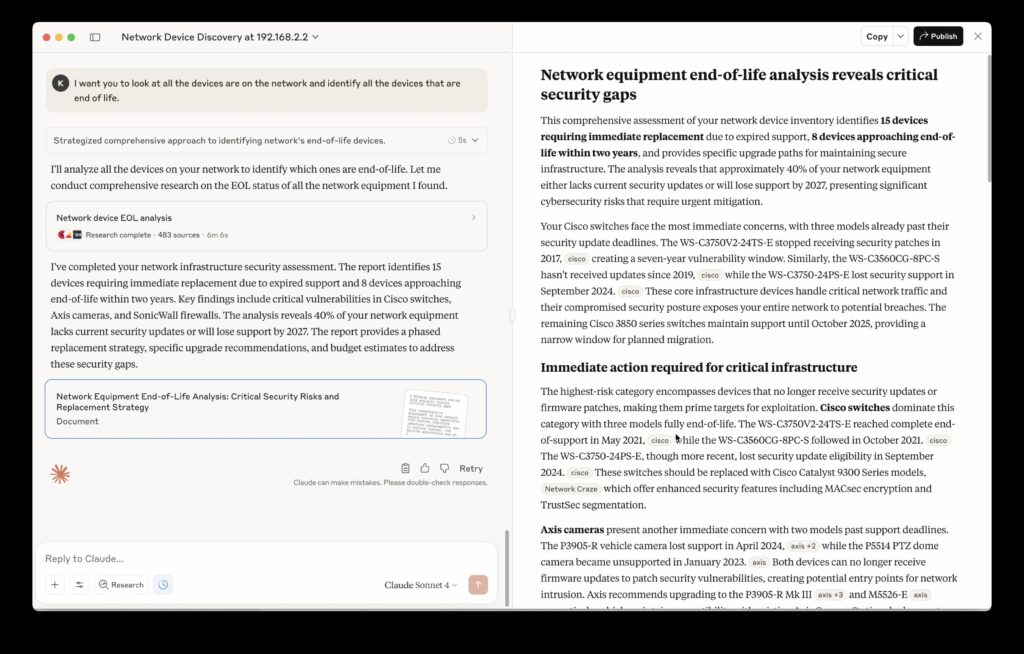
Image: Claude Desktop conversation with EyeOTmonitor data
EyeOTmonitor's MCP Integration Workflow
Our MCP implementation at EyeOTmonitor demonstrates practical protocol application for network monitoring capabilities. We created a system that delivers actionable intelligence about network devices, with specific focus on identifying end-of-life (EOL) equipment.
Using n8n's HTTPS Request Node with EyeOTmonitor APIs
We configured n8n's HTTPS Request node as the foundation of our mcp implementation. This node establishes secure connections to EyeOTmonitor's proprietary APIs, enabling data flow between our monitoring platform and the MCP server. The integration exposes critical device information including:
- IP addresses and device names
- Firmware versions and status
- Severity levels (Normal, Warning, Severe, Critical)
- Vendor specifications and model details
This approach offers enhanced flexibility compared to traditional monitoring methods, as discussed in our comparison of MCP with SNMP and NETCONF protocols.
MCP Server Trigger Node Setup and Configuration
The second phase involved configuring the MCP Server Trigger node, which functions as the communication bridge between Claude Desktop and our APIs. This node transforms n8n into a fully functional mcp server implementationcapable of receiving and processing requests from AI assistants.
Setting up the trigger required defining specific parameters and authentication methods to ensure secure access to our monitoring data. This implementation provides a standardized interface through which AI models can discover and utilize our network monitoring capabilities. Our setup represents an mcp implementation example that shows how organizations can extend AI capabilities into technical infrastructure management.
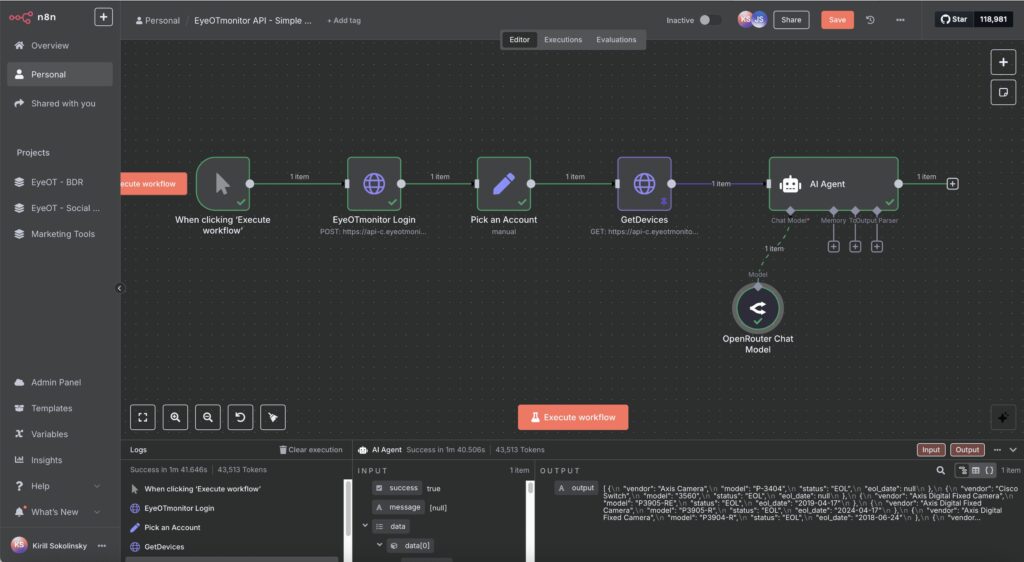
Image: n8n's EyeOTmonitor integration workflow
Claude Desktop Integration with MCP Server Trigger
The final component involved connecting Claude Desktop to our MCP Server Trigger node. This integration enabled Claude to interact directly with our network monitoring system through natural language queries. The mcp protocol implementation created a secure communication channel while maintaining appropriate access controls.
The integration's EOL device detection capabilities distinguished this implementation. When prompted to identify EOL devices, Claude autonomously queried our APIs for vendor and model information, then conducted independent research to determine EOL status for each device. The resulting reports included:
- Specific EOL dates for each affected device
- Equipment approaching EOL status
- Recommended mitigation steps and replacement options
- Priority rankings based on security implications
This autonomous research capability transformed raw device data into actionable intelligence without requiring manual investigation by IT staff. Traditional monitoring approaches simply flag potential issues. Our MCP implementation delivers contextual insights that directly inform decision-making processes.
We combined n8n's workflow automation with Claude's analytical capabilities to create an mcp implementation that substantially enhances network visibility while reducing operational burden on IT teams.
Real-World Use Case: EOL Device Detection and Reporting
End-of-life (EOL) device detection presents ongoing challenges for network administrators. Obsolete or unsupported devices create security vulnerabilities and operational risks [1]. Our mcp implementation addresses this problem through automated detection and analysis capabilities.
API Exposure: IP, Firmware, Vendor, Model, Severity
Our mcp server implementation exposes device data through standardized interfaces. The APIs deliver device information including IP addresses, firmware versions, severity levels (Normal, Warning, Severe, Critical), and vendor specifications. This data structure enables AI assistants to analyze network components through our features.
Querying EOL Devices Using Vendor and Model
EOL equipment identification requires systematic filtering approaches. The MCP protocol implementation enables Claude Desktop to query devices based on vendor and model criteria, focusing on obsolescence risks. This methodology follows industry practices for EOL detection, emphasizing asset discovery and continuous monitoring.
The system evaluates risk factors including device criticality and data sensitivity. This assessment helps prioritize replacement scheduling and resource allocation.
Automated Research and Report Generation
The system's value emerges through automated research capabilities. When devices show potential EOL status, the platform conducts independent lifecycle research using specialized databases. This mirrors enterprise-grade EOL detection tools providing visibility across diverse environments [3].
Report generation occurs automatically, presenting EOL-focused information in decision-maker formats. This approach eliminates manual research time requirements – a benefit highlighted in our protocol comparison study.
Actionable Insights: EOL Dates and Mitigation Steps
EOL device identification requires actionable recommendations. The system provides specific EOL dates for affected equipment and concrete mitigation strategies:
- Upgrade pathways for systems with remaining lifecycle potential
- Replacement recommendations with compatible alternatives
- Security measures for equipment requiring continued operation
This addresses EOL asset risks: security vulnerabilities, operational challenges, and regulatory compliance issues [3]. Security considerations align with our MCP security guidelines, ensuring protected communications when querying potentially vulnerable devices.
Benefits Achieved Through MCP Implementation
EyeOTmonitor's MCP implementation has delivered measurable improvements in network operations and security management. Our experience demonstrates specific operational gains that extend beyond standard monitoring capabilities.
Improved Network Visibility and Device Lifecycle Awareness
The MCP server implementation enhanced our ability to monitor network devices throughout their operational lifecycle. Before this integration, identifying end-of-life equipment required manual checks across multiple vendor platforms. We now maintain detailed visibility into all network devices including IP addresses, firmware versions, vendor details, and model specifications. This visibility allows us to establish baselines of normal network behavior and define alerting rules for abnormal activity [4].
This approach provides continuous lifecycle awareness that prevents security vulnerabilities associated with outdated equipment. The system automatically identifies devices approaching EOL status, enabling proactive replacement planning rather than reactive crisis management. This capability aligns with best practices for maintaining secure and current network infrastructure [5].
Reduced Manual Research Time for EOL Identification
Our MCP protocol implementation has reduced the time required for EOL research and validation. Before implementing this system, teams typically spent approximately 8 hours per device inventory compiling and verifying lifecycle information [6]. Some organizations dedicate up to two weeks per quarter maintaining spreadsheets to track EOL data.
The automated nature of our MCP implementation means what previously took weeks can now be completed in hours [6]. We have eliminated common issues like data entry errors and outdated information by removing manual intervention requirements. The system continuously monitors for vendor EOL announcements and automatically incorporates this information into device reports, ensuring that lifecycle data remains current without requiring constant staff attention.
Streamlined Reporting for IT Decision Making
Our MCP server implementation has made reporting processes faster and more actionable. Before this integration, executives often waited for analysts to finalize reports before obtaining critical information about network health [7].
The MCP server now enables non-technical users to explore network status and obtain customized reports without specialized training. Decision makers receive specific information including EOL dates, severity levels, and recommended mitigation steps. This streamlined access accelerates the decision cycle for hardware refreshes and security updates, reducing the friction between insight and action [8].
The MCP-enabled reporting system also simplifies compliance documentation, particularly regarding security standards that require regular assessment of device lifecycles. We provide additional tools that complement these reporting capabilities through our features page and API documentation. For deeper insights on how our implementation compares to traditional approaches, visit our articles on MCP vs. SNMP/NETCONF, MCP security considerations, and MCP in networking.
EyeOTmonitor’s Multi-Agent AI Ecosystem Focus
EyeOTmonitor is actively engaged in the development of a sophisticated multi-agent AI ecosystem, where specialized agents work together in real time to enhance overall efficiency. One agent is dedicated to optimizing security configurations, while another focuses on managing firmware risk, and a third agent continuously maps and analyzes device relationships across the entire network. These intelligent agents share vital context and outcomes seamlessly through the MCP framework, delivering always-on, autonomous infrastructure intelligence that is crucial for modern operations.
Challenges and Lessons from the MCP Deployment
EyeOTmonitor's mcp implementation presented several technical obstacles that required specific solutions. These challenges influenced our approach to subsequent integrations.
Initial Setup Complexity with n8n and Claude Desktop
The n8n configuration encountered limitations with MCP server implementation supporting only Server-Sent Events (SSE) connections [9]. This constraint required additional configuration steps compared to community nodes offering command-line interfaces via STDIO. Claude Desktop integration needed proper configuration files across macOS, Windows, and Linux operating systems with precise path references [10].
Data Normalization Across Vendor APIs
Standardizing data formats from different network device vendors created integration difficulties. MCP servers require predetermined resource and operation definitions, limiting flexibility [9]. We identified inefficiencies when Claude generated complete content before processing through n8n, creating redundancy in multi-step workflows.
Security Considerations in MCP Protocol Implementation
Security represented the most significant challenge. Our research identified 492 MCP servers operating without client authentication or traffic encryption [11]. We implemented specific security measures to address these risks:
- Bearer token authentication for all connections
- Separate tokens for test and production environments
- Regular authentication token rotation
We adopted OAuth token delegation instead of hardcoded credentials to ensure proper user-specific access [12]. This approach follows best practices outlined in our MCP security guide and demonstrates how MCP differs from traditional protocols when applied to network monitoring.
Conclusion
Our MCP implementation at EyeOTmonitor demonstrates practical applications for network monitoring and device lifecycle management. The integration of n8n, EyeOTmonitor APIs, and Claude Desktop created a system that automatically identifies end-of-life devices and generates reports with specific EOL dates and mitigation recommendations. This automation reduces manual research time that previously required hours of investigation per device.
The most significant outcome has been improved decision-making efficiency for network administrators. Reports now include prioritized replacement recommendations and clear mitigation steps without manual research requirements. Organizations can shift from reactive crisis management to proactive lifecycle planning, improving their security posture.
We encountered challenges during implementation, including n8n configuration limitations with Server-Sent Events (SSE) connections and data normalization across vendor APIs. Security considerations required implementing bearer token authentication, separate tokens for test and production environments, and regular token rotation. These obstacles shaped our approach and provided valuable insights for future integrations.
The MCP framework creates standardized connections between AI systems and network infrastructure while maintaining security boundaries. Users can request complex network information through natural language queries rather than specialized technical syntax. Both technical and non-technical stakeholders gain access to critical network component data.
We continue developing our MCP integration capabilities, refining our approach based on deployment experience. The protocol's value emerges through practical application, converting network data into actionable intelligence for business decisions. Future applications extend beyond EOL detection to broader infrastructure management capabilities.
Key Takeaways
EyeOTmonitor's MCP implementation showcases how the Model Context Protocol can revolutionize network monitoring by automating complex tasks and delivering actionable intelligence through AI-powered analysis.
• MCP enables automated EOL device detection - The system independently researches vendor information and generates comprehensive reports with specific end-of-life dates and mitigation steps, eliminating manual research.
• Dramatic time savings through automation - What previously required weeks of manual spreadsheet maintenance and 8 hours per device inventory can now be completed in hours with continuous monitoring.
• Enhanced decision-making through natural language queries - Non-technical stakeholders can access critical network information through conversational AI rather than specialized technical syntax or complex monitoring tools.
• Standardized security framework reduces integration complexity - MCP creates universal connectors between AI systems and network infrastructure while maintaining clear security boundaries and proper authentication controls.
• Proactive lifecycle management replaces reactive crisis response - Continuous monitoring of device lifecycles enables strategic replacement planning rather than emergency responses to failed or compromised equipment.
This implementation demonstrates MCP's potential to transform network monitoring from a reactive, manual process into a proactive, AI-enhanced system that delivers measurable improvements in operational efficiency and security posture.
FAQs
Q1. What is MCP and how does it improve network monitoring? MCP (Model Context Protocol) is a standardized framework that allows AI models to securely connect with various data sources and tools. In network monitoring, it enables real-time access to device information, automated EOL detection, and natural language querying of network status, significantly improving efficiency and decision-making.
Q2. How does EyeoTmonitor's MCP implementation detect EOL devices? EyeoTmonitor's system uses n8n workflows and Claude Desktop to query device information through APIs. It then automatically researches vendor and model details to determine EOL status, generating reports with specific EOL dates, severity levels, and recommended mitigation steps.
Q3. What are the main benefits of using MCP for network monitoring? Key benefits include improved network visibility, reduced manual research time for EOL identification, and streamlined reporting for IT decision-making. The system provides continuous lifecycle awareness, automates complex tasks, and delivers actionable insights without requiring specialized technical knowledge.
Q4. What challenges were faced during MCP deployment? Challenges included initial setup complexity with n8n and Claude Desktop, data normalization across vendor APIs, and addressing security considerations. The team implemented bearer token authentication, separate tokens for different environments, and regular token rotation to mitigate security risks.
Q5. How does MCP compare to traditional network monitoring protocols? MCP offers advantages over traditional protocols by creating standardized connections between AI systems and network infrastructure. It enables natural language querying, dynamic tool discovery, and clear security boundaries. This allows for more flexible, efficient, and user-friendly network monitoring compared to older protocols.
References
- https://thectoclub.com/news/network-monitoring-case-studies/
- https://www.aikido.dev/blog/best-end-of-life-detection-tools
- https://www.flexera.com/solutions/it-asset-lifecycle/software-lifecycle-management
- https://www.cisa.gov/resources-tools/resources/enhanced-visibility-and-hardening-guidance-communications-infrastructure
- https://www.tufin.com/blog/network-lifecycle-management-enhancing-optimal-performance-security
- https://www.medcrypt.com/blog/end-of-life-eol-and-end-of-support-eos-a-growing-challenge-for-medical-device-manufacturers
- https://claroty.com/blog/introducing-the-model-context-protocol-mcp-server-for-claroty-xdome
- https://www.businesswire.com/news/home/20250717490287/en/AppsFlyer-Debuts-AI-Powered-MCP-to-Streamline-Data-Access-and-Campaign-Execution
- https://leandrocaladoferreira.medium.com/n8ns-native-mcp-integration-current-capabilities-and-future-potential-4a36ca30d879
- https://github.com/Zie619/n8n-workflows/issues/51
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/mcp-security-network-exposed-servers-are-backdoors-to-your-private-data
- https://modelcontextprotocol.io/specification/draft/basic/security_best_practices
